Active Directory Certificate Services (AD CS)
Active Directory Certificate Services (AD CS) is the server role that creates, manages, and validates secure digital certificates, offering stronger authentication and data protection than traditional passwords. It forms the Public Key Infrastructure backbone for securing communication, encryption, and digital signing across the enterprise.
What Is Active Directory Certificate Services (AD CS) and How Does It Work?
Active Directory Certificate Services (AD CS) is Microsoft’s Windows Server role for building an internal Public Key Infrastructure (PKI). As a Certification Authority (CA), AD CS issues, manages, and revokes digital certificates that bind identities to public keys—providing stronger, phishing‑resistant security than passwords for users, devices, and services.
• Strong Authentication: Supports smart cards and certificate‑based user/device logon with auto‑enrollment, enabling seamless domain authentication and 2FA.
• Data Confidentiality (Encryption): Powers SSL/TLS for HTTPS, VPN and Wi‑Fi (EAP‑TLS), and S/MIME to encrypt email and protect data in transit.
• Data Integrity (Digital Signing): Enables code signing and document/email signing to verify origin and prevent tampering.
When a client requests a certificate, AD CS validates identity against Active Directory Domain Services (AD DS) and, if approved, issues the cert. Because the CA’s root is trusted by domain members (via Group Policy), services relying on these certificates are automatically trusted. An internal PKI reduces cost, speeds issuance, enforces custom policies, and streamlines lifecycle management (auto‑renewal, CRL/OCSP) versus using third‑party CAs for internal needs.

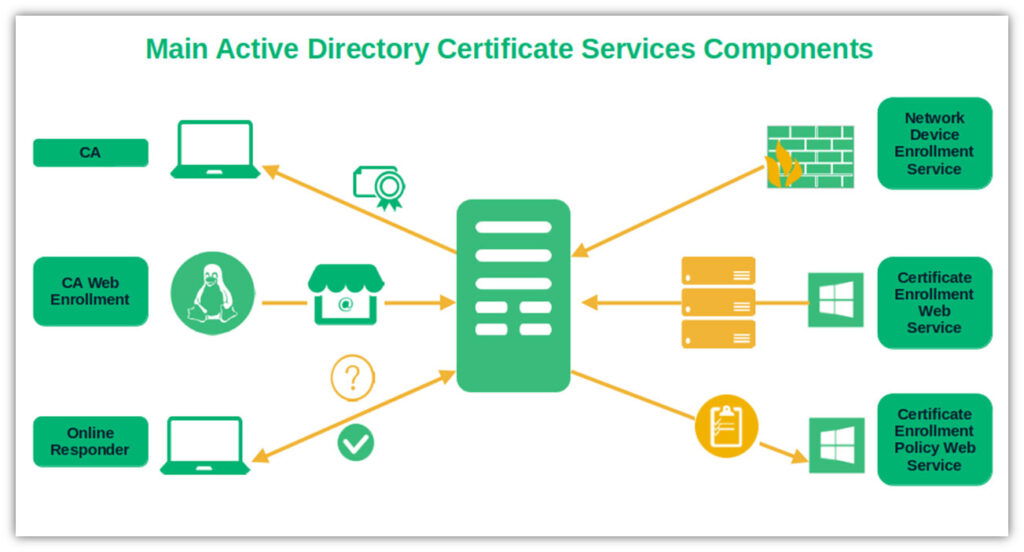
Key Components of Active Directory Certificate Services (AD CS)
The AD CS architecture is modular, with integrated roles that manage the full digital certificate lifecycle in an enterprise PKI.
Certification Authority (CA): Core service that issues, revokes, and manages X.509 certificates.
Root CA: Offline, self-signed trust anchor that signs Subordinate CAs to establish the chain of trust.
Subordinate (Issuing) CA: Handles day-to-day issuance to users, computers, and servers under the Root CA.
Certificate Enrollment Web Service: Browser-based enrollment for non-domain or non-Windows clients and external users.
Certificate Enrollment Policy Web Service: Publishes enrollment policies enabling auto-enrollment and renewal for domain-joined devices.
Online Responder (OCSP): Real-time revocation status checks without downloading large CRLs, improving performance and security.
Network Device Enrollment Service (NDES): SCEP-based enrollment for routers, switches, and appliances, supporting 802.1X/Wi‑Fi and VPN scenarios.

Step-by-Step Overview: How AD CS Issues and Manages Digital Certificates
The Process of issuing and managing certificates via AD CS is highly automated, especially for domain-joined entities.
Temple Definition: Admin defines a certificate template (key usage, validity, subject, and permissions) and publishes it for eligible users/groups.
Client Request: Domain-joined clients auto-enroll based on published templates; non-domain devices enroll via the Certificate Enrollment Web Service or NDES/SCEP.
CA Processing and Verification: The issuing CA validates identity and group membership against AD DS and template ACLs before approving the request.
Key Generation and Signing: The client generates and protects the private key locally (e.g., TPM/smart card); the CA signs the X.509 certificate with its private key.
Certificate Distribution: The signed certificate is returned to the client and can be published to AD for discovery; GPOs handle trust chain deployment and auto-renewal.
Revocation and Validation: Compromised or retired certs are revoked; CRLs and OCSP provide status checks so clients can verify validity during TLS, VPN, or Wi‑Fi auth.
Supported Windows Server Versions for Active Directory Certificate Services
Active Directory Certificate Services (AD CS) is a mature Windows Server PKI role; the server version dictates features, security, and support lifecycle.
Windows Server 2003 / 2008: Core PKI only; end of support; missing modern security—migrate immediately to mitigate risk.
Windows Server 2008 R2 / 2012 / 2012 R2: Introduced Certificate Enrollment Web Service/Policy Web Service and easier auto‑enrollment; now in extended/ended support.
Windows Server 2016 / 2019: Adds modern cryptography (e.g., SHA‑256+, ECC), improved manageability, and better virtualization/cloud integration; recommended enterprise baseline.
Windows Server 2022: Latest hardening and certificate management improvements with stronger hybrid identity alignment; longest support window.
Best practice: Use the newest LTSC Windows Server for Root and Issuing CAs to maximize lifespan, security, and current cryptographic standards.

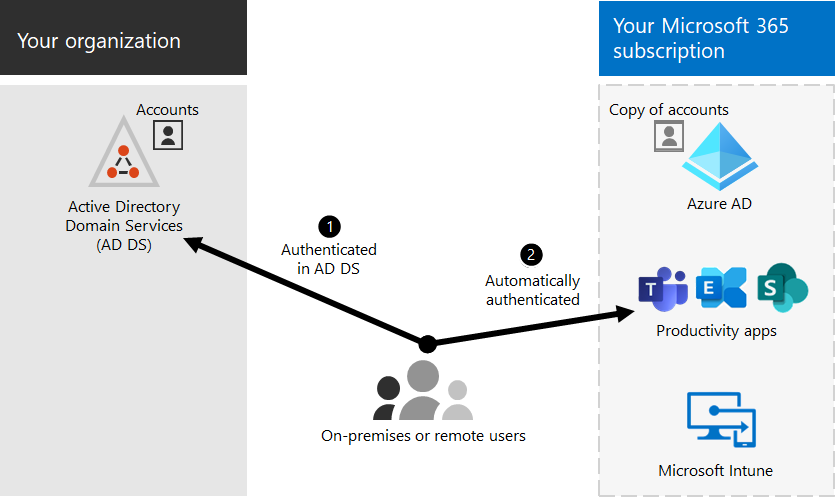
Integrating AD CS with Active Directory Domain Services (AD DS) and Other Microsoft Tools
The power of AD CS lies in its deep integration with the Microsoft ecosystem, automating PKI deployment, policy, and lifecycle management.
Integration with AD DS: AD CS links issuance to AD identities and policy, simplifying discovery and enforcing domain security.
Authentication: Uses AD DS to verify requester identity and authorization before any certificate is approved.
Auto-Enrollment: Group Policy pushes trusted roots and auto-triggers enrollment/renewal based on security group membership.
Template Publication: Publishes certificate templates and CRLs in AD DS so clients and services can discover policies and revocation data.
Integration with Group Policy: GPOs define trusted CAs, CRL/OCSP validation settings, and enforce certificate-based authentication at scale.
Integration with Exchange Server: Issues TLS certs for Exchange services and S/MIME certs to users for encrypted and signed email.
Integration with Internet Information Services (IIS): Supplies SSL/TLS for HTTPS and supports direct enrollment via the IIS certificate wizard.
Integration with System Center Configuration Manager (SCCM/MECM): Uses AD CS certs to secure client–site communications, with deployment and compliance reporting.
Understanding Single Sign-On (SSO)
Top Benefits of Using AD CS for Enterprise Security and Identity Management
AD CS: Provides a scalable, cost-effective, and highly secure PKI foundation for enterprise-level security beyond passwords.
Stronger Authentication (Beyond Passwords): Certificates enable smart card logon and certificate-based Wi‑Fi/VPN (802.1X/EAP‑TLS), delivering phishing-resistant MFA without external cloud services.
Secure Communication (TLS/SSL): Issue internal SSL/TLS certificates for websites, APIs, and apps to encrypt traffic, control the trust chain, and avoid buying public certs for internal hosts.
Simplified Management via Auto-Enrollment: With AD DS and Group Policy, users and devices auto-enroll and auto-renew certificates before expiry, reducing outages, help desk load, and admin overhead.
Data Integrity and Non-Repudiation: Enable S/MIME, document signing, and code signing to verify origin, prevent tampering, and satisfy compliance and audit requirements.
Centralized Control and Cost Savings: Run your own CA to centralize policies, issuance, and revocation (CRL/OCSP), cut certificate spend, and maintain full governance over the certificate lifecycle.
Limitations and Common Challenges of Active Directory Certificate Services
AD CS Challenges: While AD CS is robust, its complexity and operational dependencies present organizational challenges.
Operational Complexity and Maintenance Overhead: Deploying a secure multi-tier PKI (Root, Intermediate, Issuing) requires specialized crypto skills; ongoing CRL management, OCSP monitoring, and template hygiene add continual admin load.
Root CA Security: The offline, standalone Root CA is the trust anchor; compromise collapses the entire chain, and offline storage adds maintenance and disaster-recovery logistics.
Reliance on Active Directory Domain Services (AD DS): Tight AD integration means AD issues or GPO/connectivity problems can undermine identity checks and disrupt auto-enrollment at scale.
Certificate Lifecycle Management: Even with auto-enrollment, tracking issuance, renewal, and revocation for non-domain devices and external services is hard—missed renewals cause outages and warnings.
Client Trust for Non-Domain Devices: BYOD, guest, and Linux endpoints don’t inherently trust the Root CA; admins must deploy the root certificate to establish trust, adding friction.
Best Practices for Deploying and Managing AD CS in Your Organization
AD CS Best practices: Secure your PKI with a hardened hierarchy, strong crypto, and constant monitoring.
Implement a Two-Tier PKI Hierarchy: Keep the Root CA offline and use online Issuing CAs for all certificate operations.
Secure Private Keys: Protect all CA keys using HSMs, disk encryption, and strict physical access controls.
Use Strong Cryptography: Mandate current algorithms like SHA-2 and disable all legacy cryptographic standards.
Govern Certificate Templates: Strictly control enrollment permissions and enforce short certificate validity periods.
Publish Certificate Revocation: Ensure high availability of CRL and OCSP services for rapid certificate invalidation.
Audit and Monitor Continuously: Constantly review CA logs and permissions to detect and prevent unauthorized activity.
Types of Certificates You Can Issue with Active Directory Certificate Services (AD CS)
AD CS Certificate Types: AD CS uses templates to issue various X.509 certificates, securing enterprise resources through a central PKI.
Server Authentication (SSL/TLS): Secures web servers and services with SSL/TLS certificates to encrypt traffic and validate server identity.
Client Authentication: Authenticates users and devices for secure network access (Wi-Fi, VPN) and smart card logon, providing phishing-resistant MFA.
Email Security (S/MIME): Secures communications with S/MIME certificates for digital signing and end-to-end email encryption.
Code Signing: Signs applications and scripts to verify publisher identity and ensure code integrity, preventing tampering.
Domain Controller: Automatically issued to Domain Controllers to enable LDAPS and secure Active Directory replication traffic.
Encrypting File System (EFS): Allows users to encrypt files and folders on their workstations, protecting sensitive data at rest.
Frequently Asked Questions
What is the Active Directory Certificate Services?
Active Directory Certificate Services (AD CS) is a Windows Server role that allows an organization to create and manage its own internal Public Key Infrastructure (PKI) for issuing, managing, and validating digital certificates.
What is the difference between AD CS and AD DS?
AD DS (Domain Services) is the core identity service that manages users and computers. AD CS (Certificate Services) is the service that issues and manages digital certificates, relying on AD DS to verify the identity and authorization of the certificate requester
What are the different types of ADCs?
In the context of AD CS, ADC can sometimes refer to the server running the certificate services role. However, the common term is CA (Certification Authority). The hierarchy typically consists of a top-level, offline Root CA and one or more online Subordinate (Issuing) CAs.
Is Active Directory a PAM tool?
Active Directory (AD DS) is an Identity and Access Management (IAM) tool. While it is not a dedicated Privileged Access Management (PAM) tool, its security features form the foundation upon which dedicated PAM solutions are built to manage and secure highly privileged accounts.
Why publish certificates in Active Directory?
Certificates are published in Active Directory (in the user/computer object or the configuration partition) so that other services (like email servers, other clients, and domain controllers) can easily discover and retrieve the public keys associated with users and devices for the purpose of encryption and secure communication.

Search, compare & buy top business software with FGRADE. Find the best deals on Microsoft 365, Zoho, Google Workspace & more. Shop smart & save big!
Office Address
AWFIS, Ground Floor, DSL abacus it park, Survey Colony, Industrial Development Area, Uppal, Hyderabad, Telangana 500039








