Active Directory Federation Services(AD FS)
Active Directory Federation Services is a service provided by Microsoft that enables Single Sign-On for users to access systems and applications located outside an organization’s network. It acts as a trusted identity provider, bridging your corporate Active Directory (AD) with external cloud services and partner applications.
What Is Active Directory Federation Services
(AD FS)?
Active Directory Federation Services (AD FS) is a security token service (STS) developed by Microsoft that runs on Windows Server. Its primary purpose is to provide federated identity management—meaning it securely allows users to authenticate once against their on-premises Active Directory and then access various services, including those hosted by external partners or in the cloud (like Microsoft 365 or Salesforce), without needing a separate username and password. AD FS achieves this by issuing security tokens based on industry-standard protocols, most commonly SAML (Security Assertion Markup Language) and OAuth/OpenID Connect.
AD FS works by establishing trust relationships between an organization's internal identity system (your Active Directory) and external service providers. The organization acts as the Identity Provider (IdP), which authenticates the user, and the external application acts as the Relying Party (RP), which trusts the identity assertion made by the IdP. This process allows organizations to maintain control over user credentials while granting seamless access to external resources, making it a critical component for hybrid and multi-cloud environments.
How Does ADFS Work?
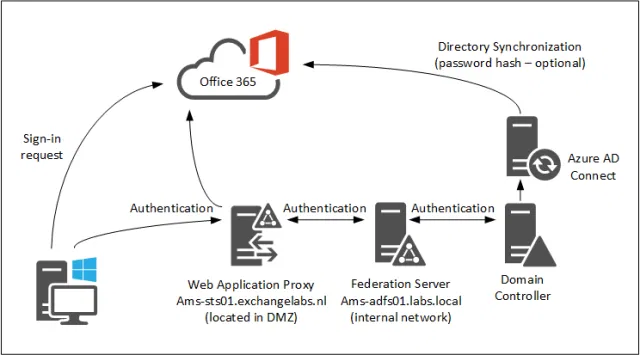
AD FS works through a series of redirected requests and token exchanges between the user's browser, the AD FS server, and the target application.
User Access Attempt: The user requests a protected, externally hosted Relying Party app, triggering AD FS’s claims-based SSO flow.
Redirection to AD FS: The Relying Party detects no session and redirects the browser to the organization’s AD FS Identity Provider via SAML or WS-Federation.
AD Authentication: AD FS prompts for credentials—or uses Integrated Windows Authentication (Kerberos) on-network—and validates them against on-premises Active Directory.
Token Creation (Claims): After authentication, AD FS gathers attributes (UPN, groups, email) and applies claims rules to define which claims are emit
Token Issuance: AD FS builds a digitally signed security token (e.g., SAML assertion) containing the claims and returns it to the user’s browser.
Token Presentation: The browser posts the issued token back to the Relying Party endpoint, resuming the original request seamlessly.
Access Granted: The Relying Party verifies the token’s signature with AD FS’s public key and grants access based on the claims (e.g., member of Sales).

ADFS Authentication Process
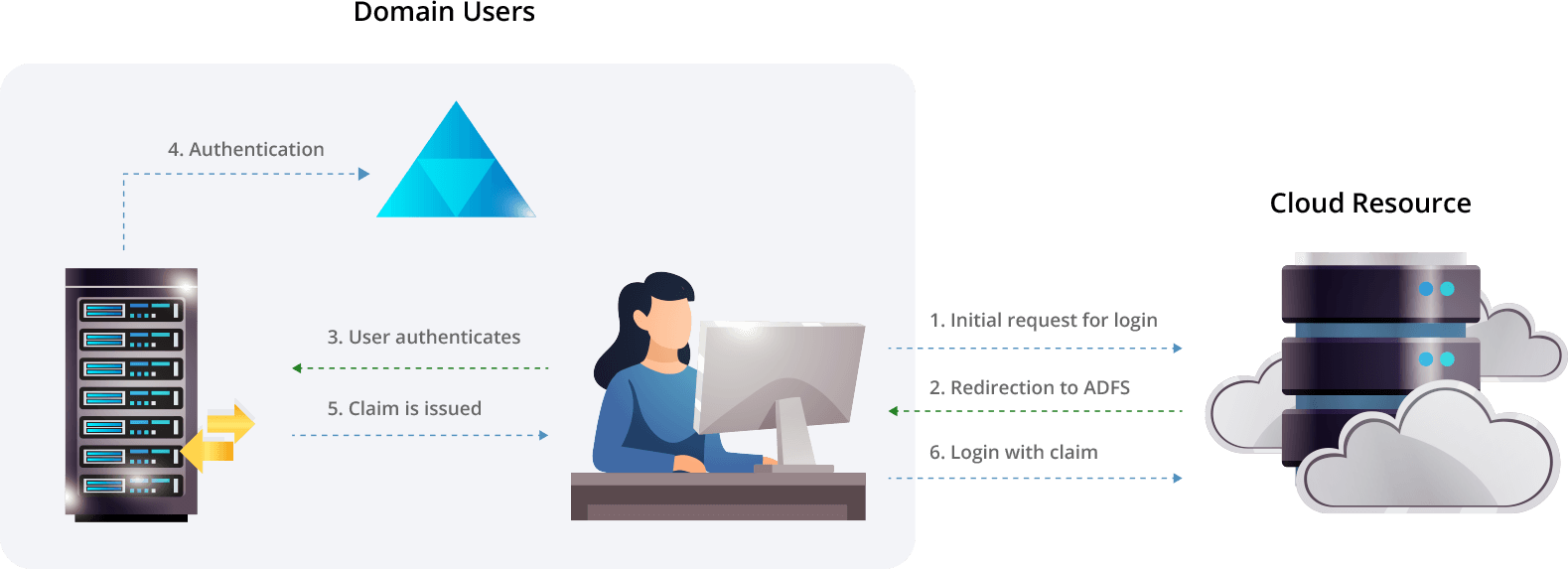
The core of the AD FS process is the secure, claims-based authentication flow.
1. Unauthenticated Access: A user attempts to open the Relying Party (RP) application without an active session, initiating the AD FS claims-based SSO flow.
2. Protocol Request: Seeing no login, the RP redirects the browser to the AD FS endpoint using SAML or WS-Federation, carrying state for a smooth return.
3. Local Authentication: AD FS presents sign-in, using Integrated Windows Authentication (Kerberos) on corporate networks or credentials/MFA for remote users.
4. Validation with Active Directory: AD FS validates credentials against on-premises Active Directory, keeping the password inside the network and enforcing policies.
5. Claims Generation: Issuance Authorization and Transform Rules map attributes (UPN, employee ID, groups) into claims (e.g., role=Finance) for authorization.
6.Token Signing and Transmission: AD FS builds a security token, signs it with its private key, and sends it back to the RP via the user’s browser over HTTPS.
7.RP Verification and Session: The RP verifies the signature with AD FS’s public key from federation metadata, trusts the token, and issues a local session.
Important Features of AD FS
AD FS is packed with features designed to facilitate secure, external identity verification and access.
1. Federated Single Sign-On: AD FS enables one-time corporate sign-in for seamless access to external, cloud, and partner apps without re-entering credentials.
2. Standards-Based Protocol Support: Supports SAML 2.0, WS-Federation, OAuth 2.0, and OpenID Connect to ensure broad interoperability with SaaS and third‑party services.
3. Claims-Based Access Control: After AD verification, AD FS issues tokens with attributes (name, email, group membership) so Relying Parties can enforce granular, attribute-based authorization.
4.Multi-Factor Authentication Integration: Integrates with leading MFA providers to require a second factor before token issuance, strengthening security for remote and sensitive access.
5.Device Registration: Registers corporate and BYOD devices so policies can assess device compliance and issue tokens based on both user identity and device posture.
6.Trust Management: Lets admins establish and govern trusts with Claims Providers and Relying Parties, defining which claims are issued, transformed, and accepted.
Why Do Organizations Use ADFS?
Organizations utilize AD FS primarily to enable secure, enterprise-wide access to modern cloud and partner applications while maintaining centralized control over identity.
1. Enabling Cloud Adoption (Hybrid Identity): AD FS bridges on‑premises Active Directory with Microsoft 365 and SaaS apps, enabling hybrid identity and secure SSO to cloud resources using existing corporate credentials.
2. Security and Compliance: By centralizing authentication in on‑prem AD, AD FS enforces policy, removes duplicate external passwords, and instantly revokes federated access upon account disablement to meet audit and compliance.
3. External Partner and Customer Access: AD FS federates with partner identity providers so external users access shared resources with their own credentials, reducing guest account overhead and streamlining B2B collaboration.
4. Custom Access Control Logic: AD FS claims rules deliver granular, attribute‑based authorization using AD data (group membership, device posture, IP), applying conditional access per app and user context.
Understanding Active Directory Federation Servicest
AD FS Benefits for End Users
AD FS simplifies and secures sign-in to deliver a smoother, safer user experience.
• True Single Sign-On (SSO): Users sign in once and access cloud, partner, and corporate apps without re-entering passwords, boosting productivity.
• Fewer Passwords to Manage: One strong corporate password reduces fatigue and risky behaviors like reuse or writing passwords down.
• Seamless Access to Resources: With Integrated Windows Authentication on the internal network, users get zero-prompt access (e.g., Microsoft 365) as AD FS issues tokens in the background.
• Consistency and Reliability: If users can log in to their computer, they can access work apps via the same consistent, AD-based authentication.
AD FS Benefits for Organizations
AD FS delivers strategic and operational value beyond basic SSO.
• Cost Reduction and Centralized Governance: Consolidates identity in AD, cuts password-reset tickets, lowers ops costs, and centralizes access to the corporate source of truth.
• Enhanced Security Policy Enforcement: Extends MFA, password complexity, and lockout policies to cloud apps, strengthening security and compliance.
• Fexible Trust Framework: Claims rules enable fine-grained, policy-driven access (group, device, IP)—e.g., only Senior Management on corporate devices.
• Extensibility and Modernization: Native OAuth 2.0/OpenID Connect support secures modern web and mobile apps and prepares the platform for future needs.
ADFS Limitations and Disadvantages
• Despite its power, AD FS has limitations that lead many organizations to consider cloud‑native alternatives.
• Infrastructure and Complexity: Requires redundant AD FS and WAP servers (plus load balancing), driving hardware, licensing, and ongoing maintenance.
• High Maintenance Overhead: Needs specialized setup, claims‑rule authoring, patching, and certificate management—errors or expirations can halt all federated access.
• Dependency on On-Premises AD: Outages in local AD or AD FS instantly block access to all federated external services.
• Hybrid Identity Bridge: As a bridge to the cloud, it ties external access to on‑prem health, lagging cloud‑native identity in resilience and agility.
Is There a Better Alternative to ADFS?
For cloud-first organizations, Azure Active Directory (Azure AD) is the preferred alternative—a cloud-native IAM that issues tokens directly without on-prem servers.
• Simplified Infrastructure: Azure AD eliminates AD FS and WAP servers, cutting hardware, maintenance, and patching overhead.
• True Cloud Native: Delivers elastic scale, built-in high availability, and global redundancy; access isn’t tied to local network or server health.
• Modern Protocols: Secures cloud, mobile, and legacy apps with SAML, OAuth 2.0, and OpenID Connect on a unified platform.
• Synchronization vs. Federation: Azure AD Connect syncs identities/password hashes so Azure AD authenticates directly—simpler and more reliable than AD FS redirects.
Conclusion
While AD FS may still be necessary for complex legacy or B2B applications, Azure AD is the strategic, cloud-first platform for modern identity management.
FAQs
ADFS Limitations And Disadvantages?
The main disadvantages are the high cost and complexity of maintaining the required infrastructure, the dependency on the on-premises network for cloud access, and the steep learning curve required for configuring its claims rules.
What is the difference between AD and ADFS?
AD(Active Directory) is the database and master identity store for the corporate network. AD FS(Active Directory Federation Service) is the service that reads identity information from AD and issues security tokens to grant access to external cloud and partner applications.
Is ADFS the same as LDAP?
No. LDAP is a protocol. AD FS is a service that uses a user’s identity to issue tokens for federated access. AD FS uses LDAP internally to read user attributes from AD.
What are the three types of directory services?
The three common types are Hierarchical/Centralized (like Active Directory/LDAP), Distributed (like DNS), and Cloud-Based (like Azure Active Directory).
Which is better, LDAP or SSO?
They are not comparable. LDAP is a protocol (a language) used for communication. SSO (Single Sign-On) is a feature (a user experience outcome). LDAP is one of the underlying protocols that can be used to enable the SSO feature
What is AAA in Active Directory?
AAA stands for Authentication, Authorization, and Accounting. Active Directory is primarily responsible for the first two: Authentication (verifying identity) and Authorization (determining access permissions). Accounting (logging and tracking resource usage) is typically done by separate logging/auditing tools.
What is FFL and DFL in AD?
FFL stands for Forest Functional Level, and DFL stands for Domain Functional Level. These are settings that determine the available features in Active Directory, based on the oldest version of Windows Server operating on the domain controllers (e.g., setting a DFL to Windows Server 2016 enables features specific to that version).

Search, compare & buy top business software with FGRADE. Find the best deals on Microsoft 365, Zoho, Google Workspace & more. Shop smart & save big!
Office Address
AWFIS, Ground Floor, DSL abacus it park, Survey Colony, Industrial Development Area, Uppal, Hyderabad, Telangana 500039
