Lightweight Directory Access Protocol (LDAP) | FGRADE
LDAP is a vendor-neutral protocol that enables users, applications, and devices to query and modify data stored in network directory services. It is essentially a language used to talk to a directory database, making it a critical technology for managing centralized identity and access in modern IT environments
About Lightweight Directory Access Protocol (LDAP)
The Lightweight Directory Access Protocol is an open, standard application protocol used for accessing and maintaining distributed directory information services over an Internet Protocol network. It acts as a set of rules for querying and modifying the centralized information contained within a directory. Think of an LDAP directory as a highly organized, hierarchical database, like a massive corporate phone book that stores all critical network information: user names, passwords, email addresses, server locations, and security policies.
LDAP is "lightweight" because it was designed as a simpler, more efficient alternative to the older, more complex X.500 Directory Access Protocol (DAP). While DAP required a full Open Systems Interconnection (OSI) network stack, LDAP operates over TCP/IP, making it ideal for the internet and modern networks. It uses a client-server model: a client (like an application or a user attempting to log in) sends a request to an LDAP server (the directory service), which then processes the query and returns a response. LDAP’s primary function is to provide a standardized, consistent way for all network services to verify identity and find resource information, making it the language of identity management.

Understanding LDAP component
Lightweight Directory Access Protocol (LDAP) organizes and accesses data through a few core components:
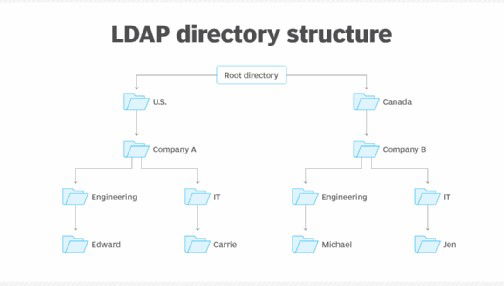
• Directory Information Tree (DIT): A hierarchical structure with the root at the top, branching into organizations, OUs, and entries. Example: dc=com → dc=Microsoft → ou=Users → individual entries.
• Entries and Attributes: An entry represents an object (like a user or printer). Attributes store details about it, such as cn, mail, or userpassword.
• Distinguished Name (DN): A unique path identifying each entry, e.g., cn=John Doe, ou=Sales, dc=company, dc=com.
• Relative Distinguished Name (RDN): The part of the DN that identifies the entry within its parent container (e.g., cn=John Doe).
• Schema: Defines the structure—what object classes exist, required/optional attributes, and allowed values—ensuring consistency across the directory.
Why LDAP?
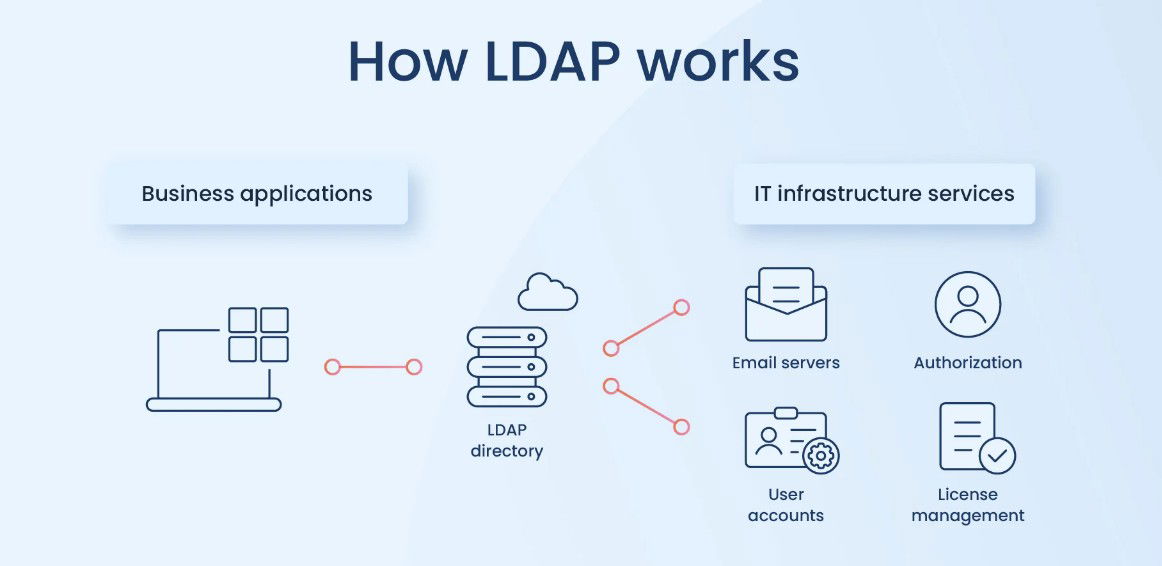
Lightweight Directory Access Protocol (LDAP) solves the problem of scattered identity management by centralizing user and access control.
• Centralized IAM: All user, group, and resource data is stored in one directory, making onboarding, offboarding, and access updates simple.
• SSO Enabler: Users log in once to access multiple LDAP-aware services like email or VPN, improving security and productivity.
• Vendor Neutral: As an open standard, LDAP works across Windows, Linux, macOS, and third-party platforms, ensuring broad compatibility.
• Security and Auditing: Centralization allows consistent password policies and easy monitoring of access activity for compliance and threat detection.
How Does LDAP Authentication Work?
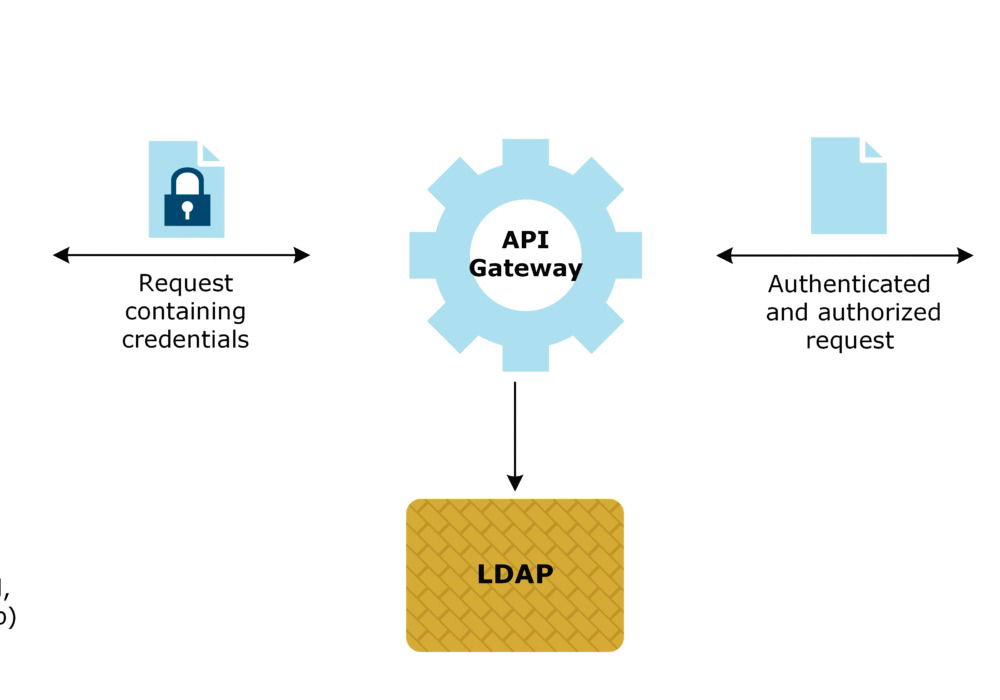
Lightweight Directory Access Protocol (LDAP) authentication verifies a user or application against a central directory in two main steps: bind and search.
Bind (Authentication): The client connects to the LDAP server with a Distinguished Name (DN) and password.
Simple Bind uses DN and password over a secure LDAPS connection.
Kerberos/SASL Bind allows authentication without sending the password directly.
If credentials match, the bind succeeds; otherwise, access is denied.
Search (Authorization): After authentication, the client queries the directory for attributes like group memberships. Applications use this info to decide access levels (read, write, admin).
This clear split between authentication and information retrieval makes LDAP secure and efficient for managing access.
LDAP Vs Active Directory
The relationship between Lightweight Directory Access Protocol (LDAP) and Active Directory (AD) is best understood as the difference between a language and an operating system. LDAP is a protocol—a set of rules and formats for communication—while Active Directory is a full-fledged directory service that functions as both software and a database. LDAP provides the language for querying and modifying a directory, whereas AD delivers centralized Identity and Access Management (IAM). LDAP is an open, vendor-neutral standard used by various systems like OpenLDAP and Novell eDirectory, while AD is proprietary to Microsoft Windows Server environments. For authentication, LDAP typically uses simple bind operations, while AD primarily relies on Kerberos for more advanced authentication but still exposes an LDAP interface. Structurally, LDAP defines a simple, hierarchical Directory Information Tree (DIT), whereas AD builds on this with a more complex architecture of domains, trees, forests, and Group Policy Objects (GPOs).
Discover how LDAP can streamline your business
Reach out to the FGRADE Concierge Team for a free consultation!
Call Us
+91 916 056 5554
Mail Us
sales@fgrade.com
Why Choose FGrade?
01
Migrations
FGrade handles seamless migrations to ensuring your data is transferred accurately and securely. Our successful track record speaks for itself.
02
Certified Experts
Our team comprises certified professionals with extensive training in all IT products. Trust us to manage your HR systems with the utmost expertise.
03
Great Price Discounts
At FGrade, we're ready to help you customizing workflows, setting up approvals all these at lower prices.
Frequently Asked Questions
What is LDAP authentication?
LDAP authentication is the process of verifying a user's identity by having a client (user or application) send their credentials (Distinguished Name and password) to an LDAP server via the LDAP protocol.
How does LDAP authentication work?
It works through a "bind" operation. The client attempts to bind to the LDAP server using the credentials. If the server successfully verifies the credentials against the directory database, the bind is accepted, and the user is authenticated.
What are the two forms of LDAP authentication?
Yes, Writer allows you to open, edit, and save MicrosoftThe two main forms are Simple Bind (where the client sends the DN and password to the server, ideally over an encrypted connection like LDAPS) and SASL Bind (which uses advanced mechanisms like Kerberos or Digest-MD5 to prove identity without sending the password directly) Word documents seamlessly.

Search, compare & buy top business software with FGRADE. Find the best deals on Microsoft 365, Zoho, Google Workspace & more. Shop smart & save big!
Office Address
AWFIS, Ground Floor, DSL abacus it park, Survey Colony, Industrial Development Area, Uppal, Hyderabad, Telangana 500039








