Active Directory Domain Services(AD DS)
Active Directory Domain Services is the core component of Microsoft’s Active Directory, providing the centralized, hierarchical structure necessary for managing all identities and resources in a Windows domain network. It is the fundamental service that handles user authentication, authorization, and the enforcement of security policies across the enterprise.
What Is Active Directory Domain Services?
Active Directory Domain Services (AD DS) is the server role in Windows Server that acts as the network’s identity management system. It stores, organizes, and manages all critical network objects—such as user accounts, computer accounts, security groups, and devices—in a single, structured, and searchable database. By implementing AD DS, an organization transforms its individual computers into a unified, centrally managed domain network.
The primary purpose of AD DS is to establish Identity and Access Management (IAM). It is responsible for authentication (verifying a user's identity, typically using the Kerberos protocol) and authorization (determining the specific resources an authenticated user is permitted to access). The dedicated servers that run this role are called Domain Controllers (DCs). This centralization simplifies IT administration, enhances network security through consistent policy enforcement, and provides users with a seamless access experience.
How Does AD DS Work?
Active Directory Domain Services (AD DS) is the central identity, security, and resource directory for Windows networks. Its database, stored on every Domain Controller, is defined by the Schema and organized as a Directory Information Tree (OUs → Domain → Forest). Authentication uses Kerberos: a DC validates credentials and issues a Ticket‑Granting Ticket for Single Sign-On (SSO). Authorization checks the user’s security token against resource Access Control Lists (ACLs). Resilience comes from multi‑master, asynchronous replication across DCs, while Flexible Single Master Operations (FSMO) roles handle conflict‑sensitive tasks. Combined with Group Policy Objects (GPOs), AD DS delivers scalable, policy‑driven access control, high availability, and compliance for enterprise environments.
Benefits of Active Directory Domain Services
Implementing Active Directory Domain Services (AD DS) is critical for any enterprise network, providing significant advantages in security, administration, and user experience.
One of the most valuable benefits is Centralized Identity and Access Management (IAM). AD DS unifies users, groups, devices, and resources in one authoritative directory, streamlining onboarding, role-based access, and instant deprovisioning from a single console—eliminating scattered local accounts.
Furthermore, AD DS dramatically Enhances Security. Using Group Policy Objects (GPOs), IT enforces consistent hardening, strong password policies, and restricted local admin rights; group-based permissions uphold least privilege and deliver auditable, compliant access.
The feature of Single Sign-On (SSO) is a massive boost to User Productivity. Users authenticate once to the domain (Kerberos) and seamlessly access approved apps, file shares, and services without repeated logins, reducing password fatigue and help desk reset tickets.
Finally, the built-in architecture of AD DS ensures Scalability and High Availability. The Domains/Trees/Forests hierarchy supports global growth, while multiple Domain Controllers and continuous replication provide fault tolerance and business continuity—if one DC fails, others automatically take over.
What Services Does Active Directory Domain Services Support?
Domain Controller
A Windows Server running Active Directory Domain Services (AD DS) that stores the directory, authenticates users via Kerberos, and replicates changes; at least one DC is required per domain.
Domain
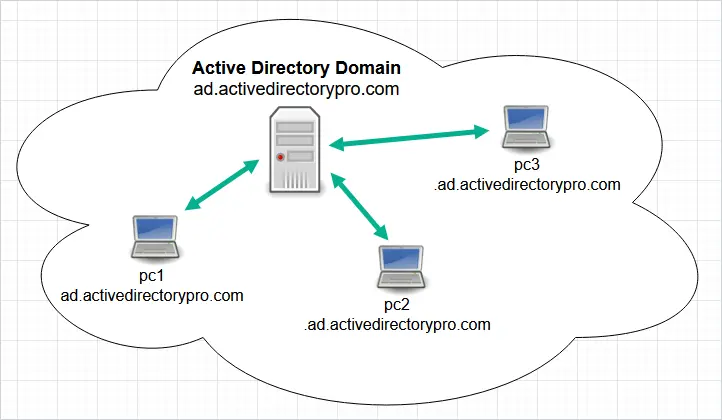
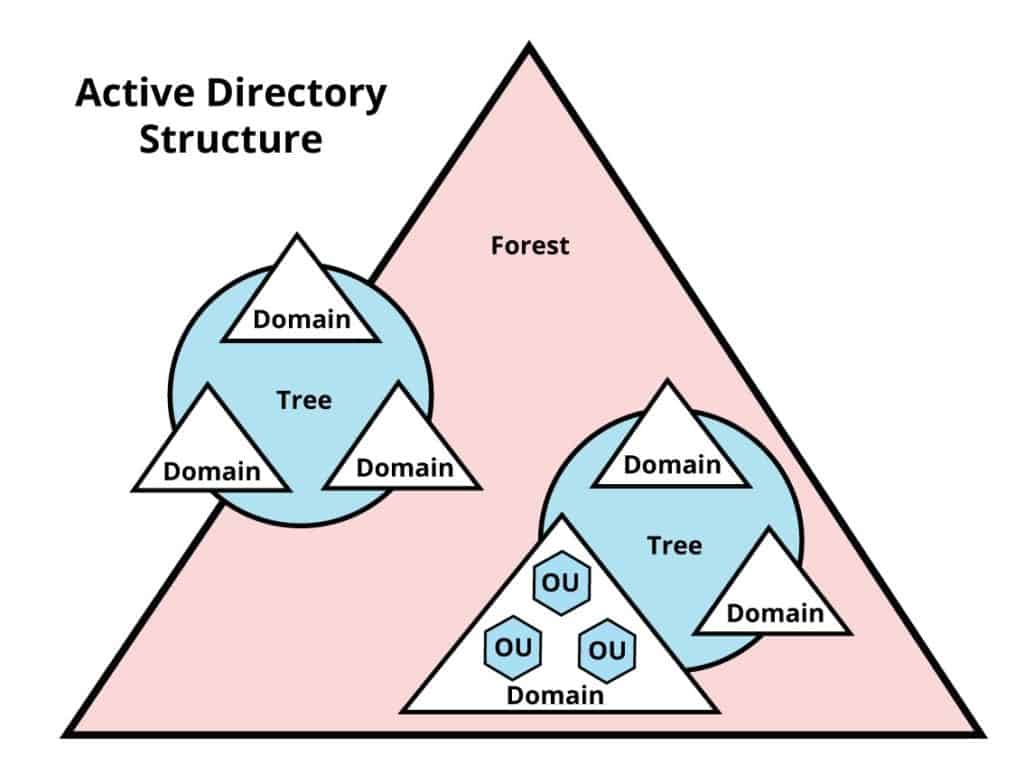
The core AD DS administrative and security boundary—a logical set of objects (users, computers) sharing a common directory database, policies, and a unique DNS name.
Forest
The top-level AD DS boundary—a collection of one or more domains sharing a single schema and configuration; all domains trust each other to form one enterprise.
Organizational Unit
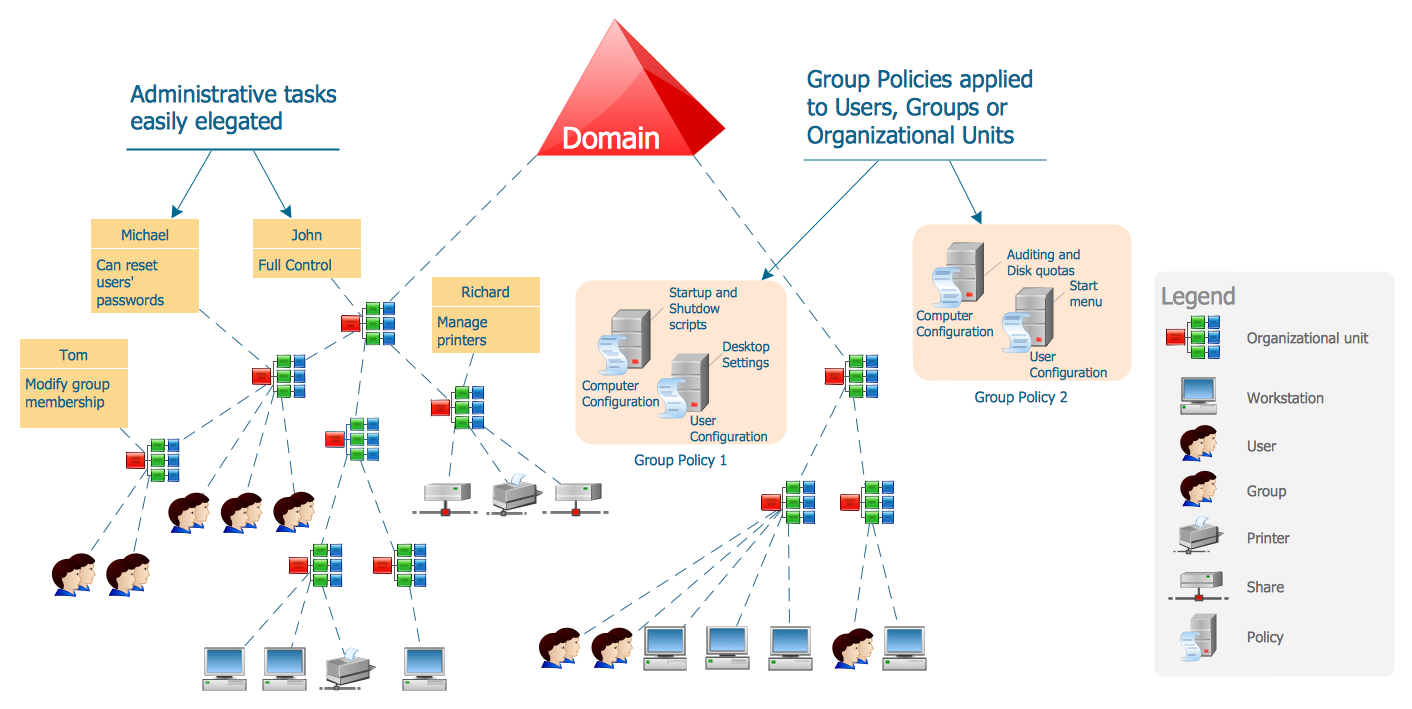
A domain container for hierarchically organizing users, groups, and computers; OUs enable delegated administration and targeted Group Policy application.
Schema
The AD DS blueprint defining object classes (e.g., user) and attributes (e.g., mail); a single, forest‑wide schema ensures consistency across all domains.
Group Policy Object
A set of configuration and security settings linked to Sites, Domains, or OUs to enforce security baselines, desktop configurations, and software deployment.
Global Catalog
A DC role holding a full copy of its domain and a partial, searchable replica of all forest objects, enabling fast directory searches and forest‑wide logons.
Active Directory Site
A group of well‑connected IP subnets representing physical locations; sites optimize client logons to local DCs and control intersite replication traffic.
What Services Does Active Directory Domain Services Support?
Active Directory Domain Services (AD DS) is the central identity plane for the Microsoft ecosystem and beyond, enabling critical network and security services.
Identity and Access Management (IAM): Provides centralized authentication (Kerberos/NTLM) and authorization for domain‑joined desktops, servers, and NAS, replacing insecure local accounts.
Group Policy Management: Hosts and distributes Group Policy Objects (GPOs) to enforce security baselines, configuration standards, and compliance across thousands of Windows endpoints.
Application Integration (LDAP): Exposes directory data via LDAP so third‑party apps, portals, HR systems, and Linux servers can query AD and authenticate with domain credentials.
Exchange and SharePoint: These platforms are AD‑aware, relying on AD DS for users, groups, and permissions; outages in AD disrupt email and collaboration.
Federation and Cloud Access (AD FS and Azure AD): AD FS issues tokens based on AD identities for SaaS; Azure AD Connect syncs identities to Azure AD for SSO to Microsoft 365 and other cloud apps.
Certificate Services (PKI): Integrated with AD CS to auto‑enroll certificates for TLS/SSL, Wi‑Fi/VPN, device trust, and smart card logon—centrally managed through AD DS.
FAQs
What is the Active Directory Domain Services AD DS schema?
The AD DS schema is the rulebook or blueprint for the entire directory. It defines the structure of the database by specifying all the object classes (e.g., a "user" object) and the attributes (e.g., "mail," "password") that those objects must or can possess.
What is the difference between AD FS and AD DS?
AD DS is the core directory service for managing internal users, authentication (Kerberos), and security policies. AD FS is a federation service that uses identity data from AD DS to issue security tokens for accessing external cloud or partner applications.
What is an ad ds domain?
An AD DS domain is the core logical grouping of network objects (users, computers, groups) that share a common AD database, a consistent administrative boundary, and uniform security policies. It is identified by a unique DNS name.
What is the main benefit of Active Directory Domain Services AD DS?
The main benefit is Centralized Identity and Access Management (IAM), which simplifies IT administration, enhances network security through uniform policy enforcement, and provides users with a seamless Single Sign-On (SSO) experience.
Is AD FS the same as LDAP?
No. LDAP (Lightweight Directory Access Protocol) is an open communication protocol (a language) used for querying and modifying directory data. AD FS is a service (a product) that uses identity data (from AD DS) to issue security tokens for federation.

